Crack The Optical Modem Superuser Password
First of all, I want to emphasize that the optical modem model is HS8545M5, and the software version is V5R020C00S200.
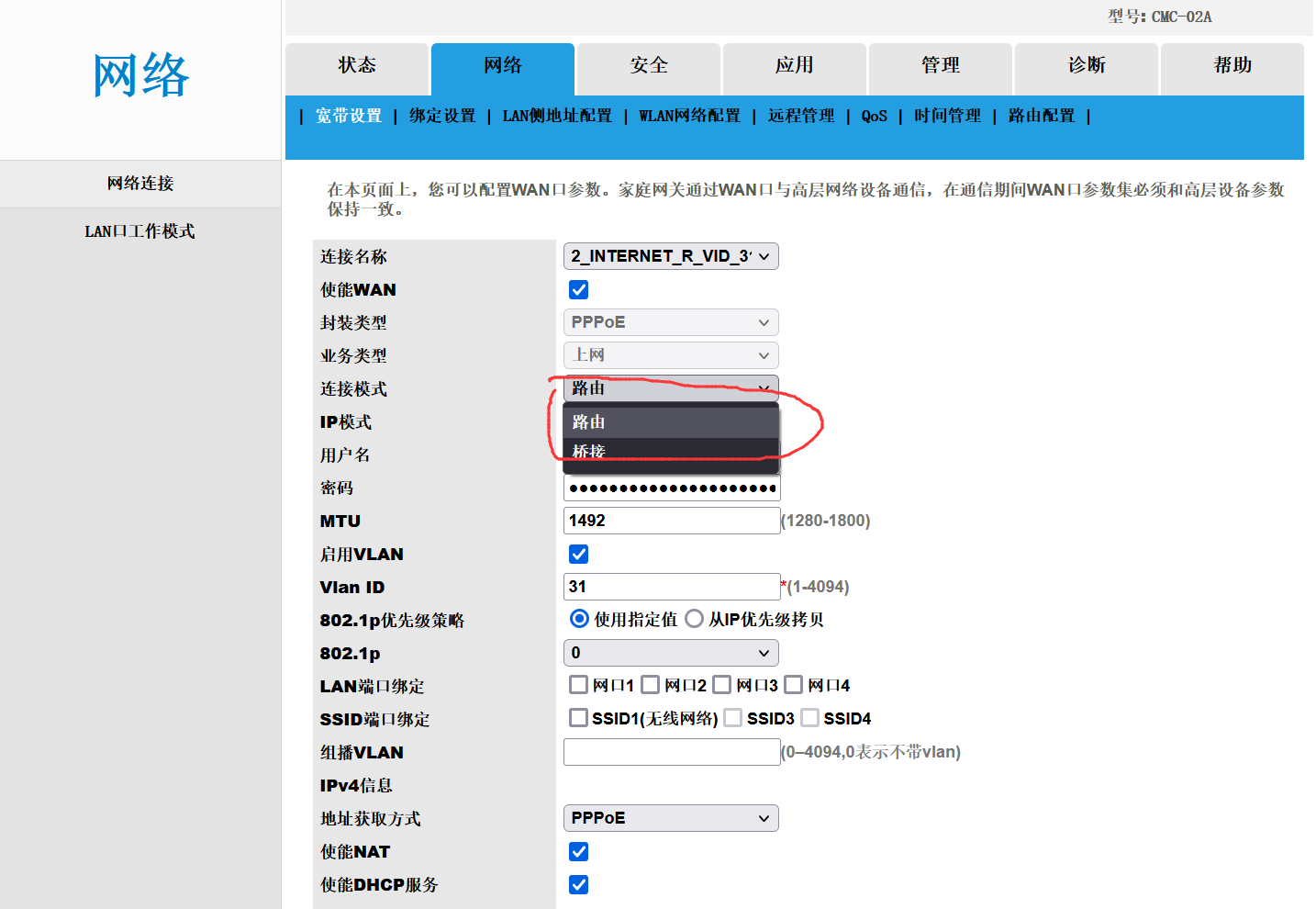
Since the optical modem needs to be in routing mode by default when it is shipped, I need to change it to bridge mode.
However, the user on the back of the optical modem does not have the permission to modify it, so I need to get superuser permissions.
Enable Telnet on the optical modem
The telnet service is not enabled on the optical modem, so we need a tool to crack it. The download link of the cracking tool is at the end.
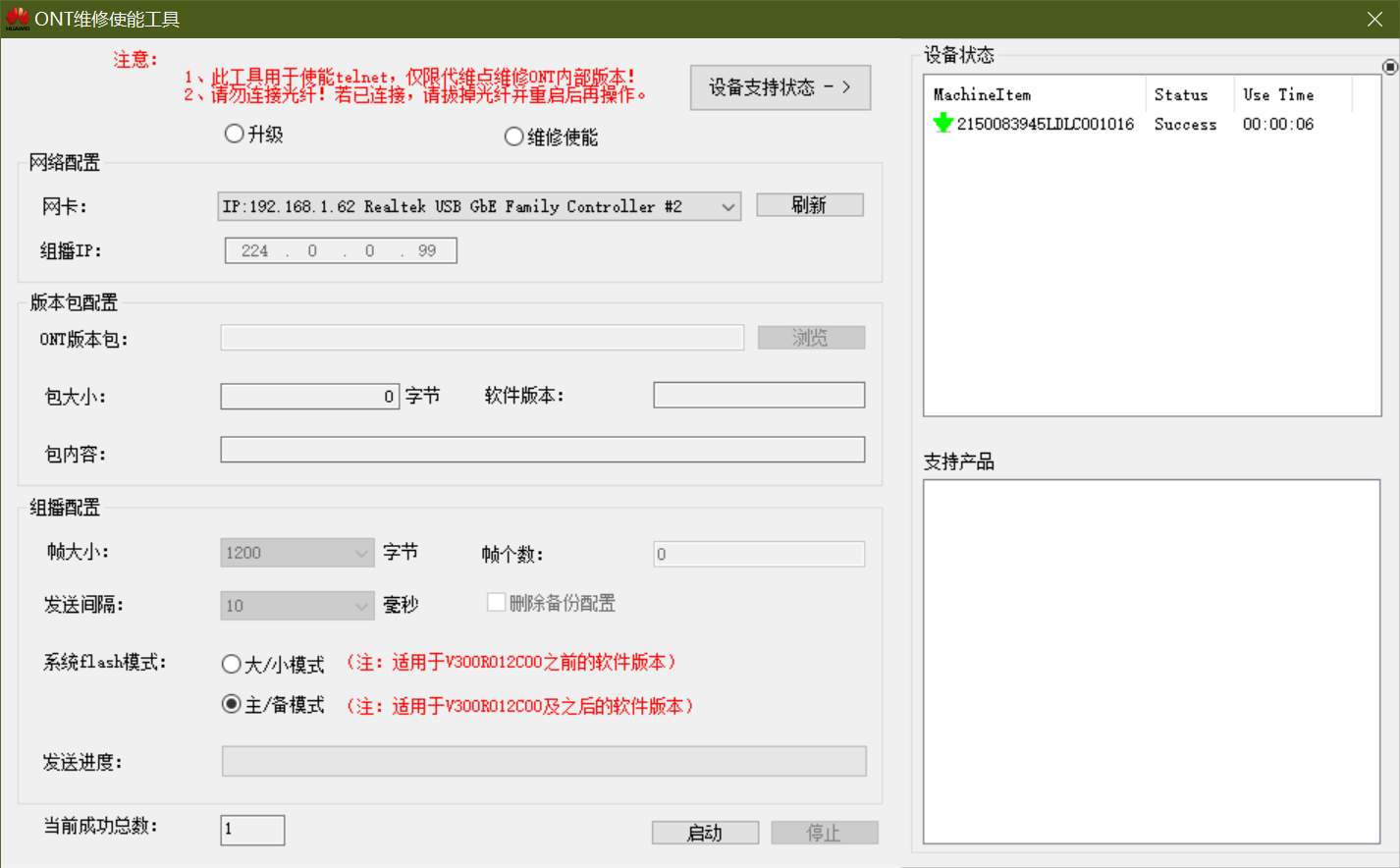
First download the cracking tool, then unplug the optical fiber, restart the optical modem, connect the computer to the optical modem via the broadband cable, and open the ONT maintenance enabling tool.
Select maintenance enabling, click refresh, and then start.
When the “current total number of successes” becomes 1, click stop, and the result is similar to the screenshot below.
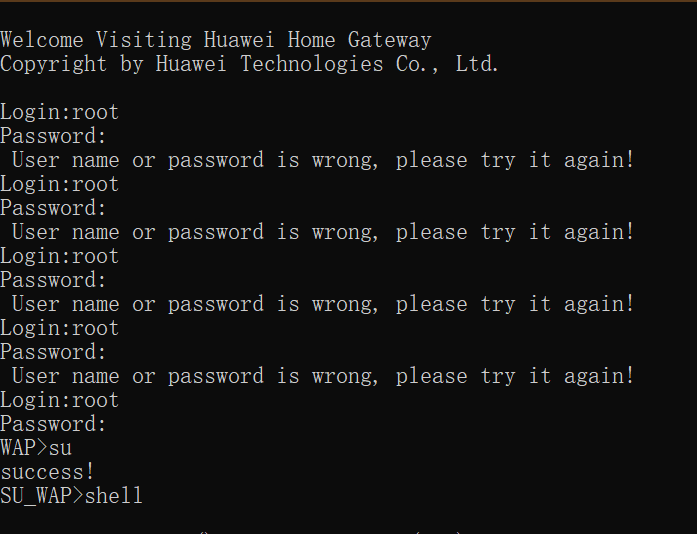
Open the command line and test whether telnet can connect successfully. If the command cannot be found, start the telnet service of Windows.
Then enter the username root; try the password Hw8@cMcc or adminHW. If successful, the result is as follows:
Get the username and password ciphertext
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
| WAP>su
success!
SU_WAP>shell
BusyBox v1.30.1 () built-in shell (ash)
Enter 'help' for a list of built-in commands.
profile close core dump
WAP(Dopra Linux) # ls
bin dev init linuxrc root sys var
boot etc lib mnt sbin tmp
bundle html libexec proc share usr
WAP(Dopra Linux) # cd /mnt/jffs2/
WAP(Dopra Linux) # ls
CfgFile_Backup dypack_debug mount_ok
CfgwithoutlineD factory_file mount_osgi_ok
DHCPlasterrwan1 fsok nffruntimes
DHCPlasterrwan5 ftvoipcfgstate oldcrc
FTCRC hard_version onlinecounter
InformFlag hw_boardinfo ontstatusfile
TelnetEnable hw_boardinfo.bak optic_init_par.bin
Updateflag_bak hw_bootcfg.xml ppplasterr258
UpnpExpandFirstInit hw_ctree.xml ppplasterr259
V5_TypeWord_FLAG hw_ctree_bak.xml reboot_bind_tag
app hw_default_ctree.xml reboot_info
asan_test hw_default_ctree2.xml recovername
backup_ok hw_hardinfo_feature request_ddr
board_type hwflashlog.bin request_ddr_inner
bob_type hwkeyinfogetlog.bin resetkey
ceaseadv.conf hwnfflog.bin restore
certs hwontdebuglogctrl.bin result_ddr
customize hwontdebuglogdata.bin scflie_0
customize.txt hwontlog.bin scflie_1
customizepara.txt keyreleasecount.txt smooth_finish
cwmp_rebootsave kmc_need_backup typeword
dhcp6c kmc_store_A upgrade_info.xml_back
dhcp_data_a kmc_store_B xmlcfgerrorcode
dhcp_lastip lastsysinfo.tar.gz
dhcpc main_version
WAP(Dopra Linux) # cp /mnt/jffs2/hw_ctree.xml /mnt/jffs2/mycfg.xml.gz
WAP(Dopra Linux) # aescrypt2 1 mycfg.xml.gz tem
WAP(Dopra Linux) # gzip -d mycfg.xml.gz
WAP(Dopra Linux) # grep WebUserInfoInstance mycfg.xml
<X_HW_WebUserInfoInstance InstanceID="1" ModifyPasswordFlag="0" UserName="user" Password="$2sN}QKqrgY(,w8^GHpW7)$|L3MQ)tWIkZv5Na2Z1E$" UserLevel="1" Enable="1" Alias="cpe-1"/>
<X_HW_WebUserInfoInstance InstanceID="2" ModifyPasswordFlag="1" UserName="CMCCAdmin" Password="$2I3^R(k3[.)B9I4E8:S!DF!Q$ULd6S(U7RRH^2]2-=Nxs&S`J6))+2$S8"'j&$" UserLevel="0" Enable="1" Alias="cpe-2" PassMode="0"/>
WAP(Dopra Linux) #
success!
SU_WAP>
|
Find the keyword user and password fields.
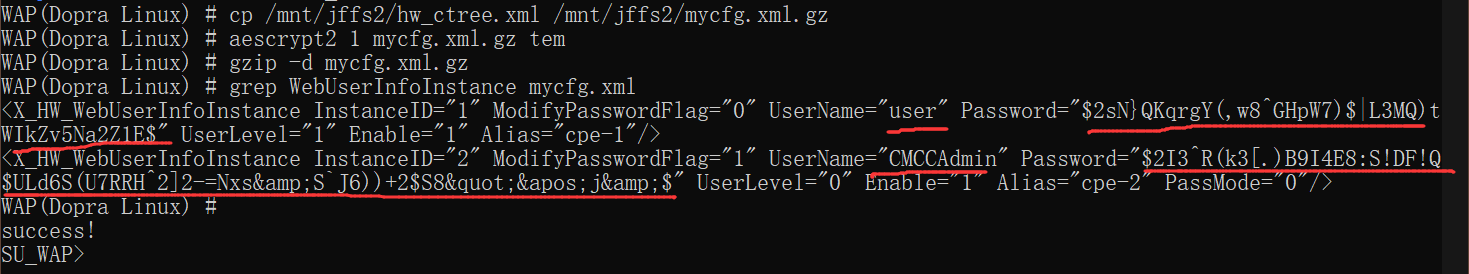
The ciphertext of the CMCCAdmin user password in the above figure is $2I3^R(k3[.)B9I4E8:S!DF!Q$ULd6S(U7RRH^2]2-=Nxs&S`J6))+2$S8"'j&$
Open the file huawei.exe in the Huawei secondary password cracking tool S1S2 Voice Full Authentication.zip, enter the password in the ciphertext decryption, try 3 decryption methods, and get the password as CMCCAdminFf2IrXFt

Log in to the optical modem as a superuser
Username CMCCAdmin, password CMCCAdminFf2IrXFt, found that the connection mode can be modified.
Downlink link:https://pan.baidu.com/s/101GrTj53T4RaIpc0h4KAoQ
Extraction code:adja
reference
- https://www.eaglemoe.com/archives/216
2022-06-18 Updated






